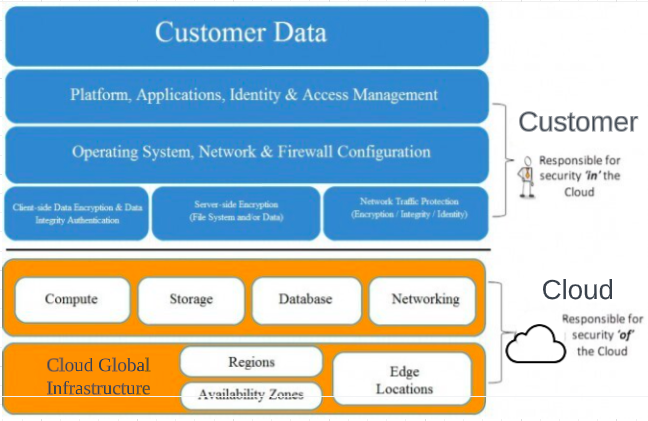
Cloud security is of paramount importance in protecting customer data, securing platform applications, managing identity and access, ensuring operating system security, and configuring network and firewall settings.
Customer Data
Protecting customer data is a critical aspect of cloud security. Cloud service providers (CSPs) must employ robust security measures to safeguard customer data from unauthorized access, loss, or disclosure. This includes implementing encryption mechanisms to protect data both at rest and in transit. CSPs should ensure that customer data is stored in secure environments, employing techniques such as data segregation and isolation to prevent data leakage or unauthorized access between customers. Regular backups, disaster recovery plans, and strict access controls are essential for maintaining the integrity and availability of customer data.
Platform Applications
The security of platform applications offered by cloud providers is crucial for protecting customer data and ensuring the overall security of the cloud environment. CSPs should implement secure coding practices during the development of platform applications to mitigate the risk of vulnerabilities. Regular vulnerability assessments, penetration testing, and code reviews should be conducted to identify and address any security weaknesses. Additionally, secure deployment and configuration practices, including secure default settings, should be followed to ensure that platform applications are protected against potential threats.
Identity & Access Management (IAM)
IAM plays a vital role in cloud security, ensuring that only authorized individuals can access resources and data within the cloud environment. Strong authentication mechanisms, such as multi-factor authentication (MFA), should be implemented to verify user identities. Role-based access control (RBAC) should be employed to assign appropriate access privileges based on job roles and responsibilities. Effective user provisioning and deprovisioning processes should be in place to ensure that access privileges are granted and revoked in a timely manner. Regular review and audit of access rights can help prevent unauthorized access and mitigate insider threats.
Operating System
Securing the operating system (OS) of cloud infrastructure components is crucial for maintaining a secure cloud environment. This involves implementing security best practices, such as regularly applying OS patches and updates, configuring secure authentication and authorization mechanisms, and disabling unnecessary services or ports. Access controls and permissions should be properly configured to prevent unauthorized access to the OS. Regular monitoring and log analysis can help detect and respond to potential security incidents in the OS.
Network & Firewall Configuration
Proper network and firewall configuration are essential for securing cloud environments. This involves implementing robust network segmentation to isolate different components and services within the cloud infrastructure. Network traffic should be monitored to detect and respond to potential threats or anomalies. Firewalls should be properly configured to enforce access control policies, filter malicious traffic, and protect against unauthorized access attempts. Regular review and update of firewall rules are necessary to ensure that they align with the organization’s security requirements.
Securing customer data, platform applications, identity and access management, the operating system, and network and firewall configuration are all crucial components of cloud security. Organizations must work closely with cloud service providers to ensure that appropriate security measures are implemented and maintained. By employing encryption techniques, implementing secure coding practices, enforcing strong authentication and access controls, maintaining a secure operating system, and configuring network and firewall settings, organizations can enhance the security of their cloud environments and protect sensitive data from potential threats. Regular monitoring, vulnerability assessments, and incident response planning should also be part of an effective cloud security strategy to detect and mitigate potential security risks.
