The Power of E-Commerce Chatbots: How LangChain and LLMs Are Transforming Online Shopping In today's fast-paced digital world, e-commerce businesses are constantly looking for ways to enhance customer experience, streamline operations, and boost sales. One of the
Blog List - Hyper Leap
- Home
- Blog List
📌 Context You’re a Java developer (likely using Spring Boot, Jakarta EE, etc.), but you need to build APIs faster—for a prototype, microservice, or edge-service. FastAPI is the Pythonic equivalent of what Spring Boot offers: declarative, fast,
As the Internet of Things (IoT) becomes increasingly accessible, building a smart, automated home is no longer limited to proprietary systems or expensive setups. With open-source solutions like Home Assistant and ESPHome, individuals and developers can create
Event-Based Autoscaling Using KEDA for Jobs on RabbitMQ In today's cloud-native world, responsiveness and efficiency are key. Workloads fluctuate—sometimes peaking rapidly—and static scaling can lead to either underutilization or outages. Event-driven autoscaling offers a smarter, more responsive
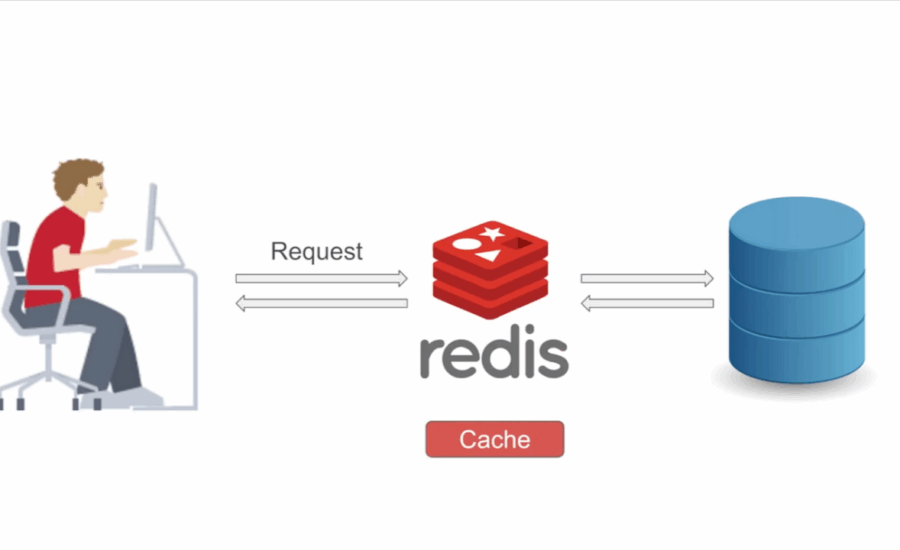
As a Java professional, when designing applications that demand high performance and responsiveness, implementing caching can significantly improve efficiency. Redis is a powerful in-memory key-value store, and Spring Boot seamlessly integrates with it. While the Spring Cache
Red Hat OpenShift: The Enterprise Kubernetes Platform In a world where containers and microservices are reshaping how we build, deploy, and scale applications, choosing the right container orchestration platform is critical. Enter Red Hat OpenShift — a
Overview Java bytecode is famously easy to decompile. While this makes Java a great language for reflection, tooling, and debugging, it also exposes your intellectual property to reverse engineering and potential misuse. Anyone with a .jar file
Introduction In the realm of cybersecurity and access control, authorization plays a crucial role in determining what users can and cannot do within a system. While authentication verifies a user's identity, authorization governs their level of access.
Near Real-Time Monitoring of Network Devices: Enhancing Performance and Security In today's fast-paced digital landscape, organizations rely heavily on network infrastructure to ensure seamless communication and data exchange. However, as networks grow more complex, the need for
Top 4 Forms of Authentication Mechanisms Authentication mechanisms play a crucial role in securing digital systems by verifying the identity of users and devices. Various authentication methods exist, each with distinct use cases and security benefits. Below,